Hello readers! Welcome to trendphobia, In today’s interconnected world, the internet serves as an essential tool for communication, shopping, banking, and much more. However, with convenience comes vulnerability, and one of the most prominent cyber threats we face today is phishing. Phishing is a fraudulent attempt to obtain sensitive information, such as passwords, credit card details or personal data, by disguising as a trustworthy entity in electronic communication. In this blog, we will explore the dangers of phishing, its various forms and essential tips to protect yourself from falling victim to these cyber traps.
Understanding Phishing

Phishing attacks usually occur through email, social media, or instant messaging platforms, where attackers create deceitful messages that prompt recipients to click on malicious links or provide sensitive information. These messages often mimic official correspondence from banks, government agencies or popular websites, making it challenging for individuals to identify the deceit.
Different Forms of Phishing
Email Phishing

This is the most common type of phishing attack. Scammers send emails that appear legitimate, urging recipients to click on links that direct them to fraudulent websites. The websites may look like well-known services such as online banking portals but are designed to steal login credentials or personal information.
Spear Phishing

In this more targeted approach, attackers research their victims to create personalized and convincing messages. They may use information from social media profiles or company websites to make the emails appear authentic, making it harder for victims to discern the scam.
Smishing

This form of phishing is conducted via SMS (text messaging). Victims receive text messages with deceptive content and links, luring them into revealing sensitive information or downloading malware onto their devices.
Also read Coffee Analysis with an Electronic Nose: Unveiling Aromas
Vishing
Short for “voice phishing,” this technique involves scammers making phone calls, often using caller ID spoofing to appear as legitimate entities like banks or government agencies. They aim to extract personal information or financial details from unsuspecting victims.
Tips to Avoid Phishing Scams
Stay Informed
Familiarize yourself with the latest phishing techniques and examples of known scams. Regularly check for updates on new tactics employed by cybercriminals to stay one step ahead.
Also read A Comprehensive Comparison: iPhone 14 vs. Samsung S23
Verify the Source
Be cautious of unsolicited emails or messages, especially those requesting sensitive information. Always verify the sender’s email address or phone number by contacting the organization directly through their official website or customer service channels.
Avoid Clicking on Suspicious Links

Hover your mouse cursor over links in emails to see the actual URL. If the link looks suspicious or does not match the sender’s claims, do not click on it.
Use Multi-Factor Authentication (MFA)
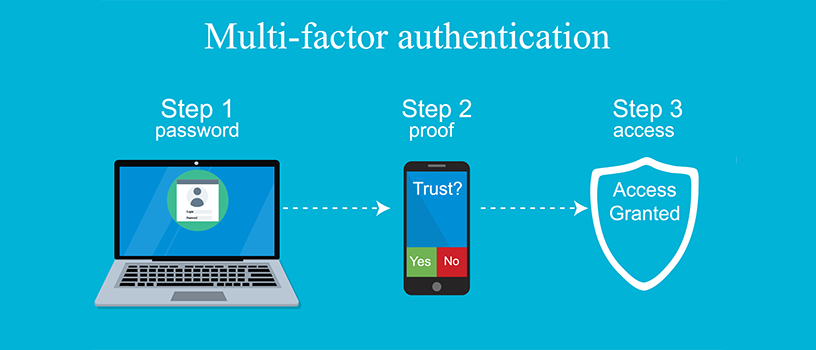
Enable MFA wherever possible to add an extra layer of security to your accounts. This ensures that even if attackers obtain your password, they would still need additional verification to access your accounts.
Keep Software Updated
Regularly update your operating system, antivirus software, and other applications. These updates often contain security patches that protect against known vulnerabilities.
According to trendphobia, Phishing is a persistent and evolving threat that can have devastating consequences for individuals and organizations alike. By being vigilant, staying informed, and following best practices for online security, you can significantly reduce the risk of falling victim to these deceptive attacks. Always remember that caution and skepticism are your best allies in the digital world. Stay safe and protect your online presence from the lurking dangers of phishing.
Thanks for reading😊
You may also read:
- The Telettrofono: World’s First Mobile Phone
- The Evolution of Apple Watch: A Journey Through All Series
- Airborne Internet: Bridging the Digital Divide
- The Pill Camera: Revolutionizing Medical Diagnostics

[…] Defeating Phishing Attacks: A Guide to Secure Online Navigation […]